Our team’s response to this popular topic within the security industry
In today’s security landscape, there’s no shortage of online resources offering advice on how we can strengthen the security of our home Wi-Fi networks. After all, home is the place where we carry out a wide array of online activities, whether related to our jobs or to what we do in our free time.
Here are a few examples from noteworthy articles on the topic:
1. Google Fiber’s Security, Privacy, & Trust team presents a snapshot of security risks associated with an unsecured home network and the steps one can (and should) take to protect their network.
2. MetaCompliance walks through some of the risks that our Wi-Fi networks can fall victim to while laying out a set of 10 tips to keep the hackers at bay.
3. WIRED explains the importance that securing your router plays in protecting your home Wi-Fi network, expanding on the significance of related practices including password hygiene and firmware updates.
The popularity of this topic shows how securing your home Wi-Fi network is paramount when it comes to safeguarding your data. We’d like to take the opportunity to build upon the ideas presented in the above articles and add some thoughts from our own team’s perspective.
High-level network vulnerabilities often found in homes
We’ve already stated that Wi-Fi networks can fall prey to a variety of attack methods, so what do these look like in practice? Here are a few common vulnerabilities that can be exploited by cybercriminals.
Piggybacking
A controversial practice in the online world, piggybacking is when someone takes advantage of someone else’s open Wi-Fi network (one that isn’t password protected) by connecting to it without the owner’s permission or knowledge. This can result in lower bandwidth or network speed.
Router malware
The router is the device at the center of your home Wi-Fi network. As mentioned in WIRED, millions of routers across the globe have come under attack by various types of malware. Attacks affecting routers include botnets, viruses, Trojans, and more.
Network capture (a.k.a. sniffing)
So-called network sniffers can be used to intercept and analyze unencrypted data that passes through a network and “sniff” the content being exchanged. Using this attack method, cyber criminals can get ahold of sensitive information including login credentials and passwords.
The abuse of Wi-Fi network services
Network services refer to each of the functions performed by IoT devices that connect to one’s network. Smart device enthusiasts likely agree that making these devices as straightforward to use as possible is a key priority. While this creates convenience and a positive user experience, it can also lead to more opportunities for vulnerabilities to be exploited.
If it appears like there is a concerningly large number of ways to attack smart devices, that’s because this is exactly the case. To put things in perspective, we collected data about the percentage of households that own various IoT devices. Here’s a look at the smart devices that connect to a typical home Wi-Fi network:
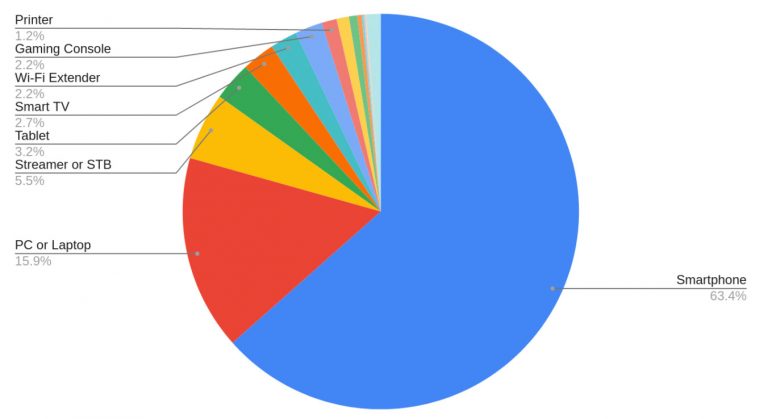
[Further reading: Internet of Things in SMB networks]
With such an array of network-connected devices to be responsible for, it can be daunting to set up and manage the solutions designed to keep them safe.
Many security solutions can add to the frustration due to complicated interfaces and functionalities. SAM solutions offer network-wide security without negatively impacting the user experience (think fast Wi-Fi connectivity, lag-free gaming, and load times).
What are the steps to achieving a secure Wi-Fi network?
Let’s go back to Google Fiber’s article. The recommendations offered are broken down into a handful of steps, listed from the easiest and most important to the most complex and least important:
- Encryption: Making your data unreadable by unauthorized parties
- Obfuscation: Securely setting up your login credentials
- Separation: Limiting access between various network-connected devices
- Authorization: Controlling who can access your network
- Rotation/validation: Keeping your network credentials fresh and secure
Although these suggestions are undoubtedly good ones, it’s important to note that taking these precautions may not be straightforward or easy for everyday users. Even the first few steps, which industry professionals may consider to be “easy” for nearly anyone, could be complicated and time-consuming for the average person — we’ll get into this is in a bit.
In response to the five steps mentioned above, we’ve added our thoughts and suggestions from our perspective as security professionals:
Step 1: Encryption
Encryption is a no-brainer for increasing network security. We agree that the least that you can do to secure your home Wi-Fi network is to encrypt your data.
Many public DNS servers (think Google or Cloudflare) offer what’s known as DNS over HTTPS/TLS, which is the encryption of DNS queries and responses over a secure HTTPS or TLS connection layer. Using this approach, cyber criminals are unable to eavesdrop on or intervene in the services that you use. With SAM’s solution, encryption is taken care of automatically. This is because SAM encrypts all of the DNS traffic that exits your network — even that of the devices that can’t encrypt it on their own.
Step 2: Obfuscation
This step is quite straightforward: Change each of your devices’ login credentials (i.e. name and admin password) from their default options!
Interested in testing out the security of a password that you have in mind? Have I Been Pwned’s password engine makes it possible to see if a given password has previously been exposed in data breaches. You can get an idea of what a secure password should look like using the large database of real-world passwords available on the page.
Step 3: Separation
Separation refers to the creation of multiple service set identifiers (SSIDs) — these can simply be understood as the network’s name. Setting up multiple SSIDs makes it possible to set aside certain devices in a “guest” network, keeping them separate from devices that permanently live inside your main home network. Separation is usually a step that individuals need to take manually, as the majority of home routers typically only support two SSIDs, which makes it possible for various smart devices to communicate with each other.
Vulnerabilities related to network devices “seeing” each other can be avoided by making use of network segmentation, which makes it impossible for unauthorized users (whether they’re cyber criminals or just curious inside users) to gain access to sensitive network data.
Using SAM solutions, users don’t need to worry about multiple SSIDs (or frankly, about the concept of SSIDs at all) due to our use of network segmentation.
We use dedicated network “zones” to classify and determine the functionality of devices within one’s home network. An IoT zone is home to smart, network-connected devices (such as smart cameras, alarms, doorbells), which functions as an effective method of separation.
More specifically, we make use of an “IoT zone” designed to house all of your network-connected devices. What’s more, our dynamic firewall and virtual patching features ensure the ongoing security of IoT devices.
Step 4: Authorization
When talking about authorization, it’s important to understand the role of media access control (MAC) addresses. These addresses are hardware identification numbers that uniquely identify each device present in a network.
It’s possible to enable authorization on your Wi-Fi network, only allowing authorized devices to access it when they’re on an approved list (related to their MAC addresses). This is known as MAC address filtering, a concept also mentioned in MetaCompliance’s article. While MAC address filtering has become the norm for most home router features (including for parental control functionalities), it can still easily be defeated by MAC randomization.
Our team has developed a tool for making authorization straightforward: our device identification allows you to view and manage all devices connecting to your network in real time, define network zones and control access using SAM Router Protection. What’s more, we make use of MAC randomization, essentially making the user untraceable across different networks.
Step 5: Rotation/Validation
In a nutshell, rotating your passwords and validation credentials makes it more difficult for hackers to wrongfully get ahold of them. In practice, rotation and validation means:
- Checking for updates
- Reviewing router logs
- Rotating your encryption key
- Changing admin credentials
While these are undoubtedly smart security practices, there’s an issue here — these can be a pain! Look no further than the average router’s firmware update manual to see what I mean.
These tasks can quickly become a headache and result in many network owners failing to carry them out. With SAM, you don’t need to worry about managing your security settings because we take care of everything in the background.
How to take a holistic approach to securing your home Wi-Fi network
All of us can agree that obtaining security for our homes and the devices inside them should be uncomplicated. While there are some great nuggets of advice out there related to protecting our home Wi-Fi networks, the fact remains that some of the suggested actions can be overly complex for the average person.
Since this topic is continually discussed by thought leaders across the cybersecurity industry, we see it as equally important for individuals everywhere to be able to rely on a security provider who will “get the job done” when it comes to staying protected.
Here’s the good news: You don’t have to do this alone.
Instead, you can lean on the expertise of security service providers to make it happen for you.
A reliable security provider takes the responsibility for you so you don’t have to actively work to maintain your security on a regular basis. We’re here to help provide a holistic experience when protecting your home Wi-Fi network.







