The US National Security Agency (NSA) recommends switching to a personally purchased router to improve network security for homes, but what about securing “all” of the devices in a home-office network? How can network service providers step in to help the average user overcome this seemingly impossible task and differentiate their offerings with real-time hot patching capabilities?
It’s a well-known fact that most home and small business devices and networks lack adequate protection. This vulnerability arises due to various reasons, including the widespread use of consumer electronic devices that have become connected IoT devices through home routers. While some vulnerabilities may only be an inconvenience for some users, others can open the door to malicious activities. One of the most pressing challenges in the realm of IoT is the sluggish discovery-to-patching process by firmware vendors, leaving users exposed indefinitely. This issue highlights a critical gap in home security, where the timely resolution of IoT vulnerabilities is of the essence.
One of the recommendations mentioned in the NSA advisory referenced above to address these security concerns is to regularly download security updates for all connected devices, and that would apply to SOHOs as well. But that is a task frankly beyond the capabilities of some, and a somewhat onerous burden for others, particularly those who are trying to run a business first and foremost!
Another interesting thing about the NSA’s guidance is the recommendation that users swap out the router provided by their network service provider in favor of one that they would purchase themselves, under the pretext presumably that a user would have more control over a device that is actually owned instead of leased. That recommendation comes from the fact that the router is the most vulnerable device within home-office networks. For hackers, router vulnerabilities present a better opportunity than any other IoT or otherwise connected device, since the router is the only gateway to all the other devices on the home network, and the only path for these devices to connect to the Internet.
So if one extends the logic of “owning your own device means greater security” throughout the entire network environment, that would mean a user would be responsible for network security comprising an average of about 20 devices. However, from what we have heard in our discussions with service providers around the world, their customers would need help in being their own “IT person” and maintaining the recommended levels of security for the router and all the connected devices.
And this “heightened awareness” environment gives network service providers an excellent opportunity to provide a tremendously valuable service – under the principle that the manager of the network connection (the router connected to the WAN), namely the ISP and MSP, is in the best position to protect all devices in the SMB/SOHO network. And that protection comes in the form of hot patching.
In our previous blog about “patching,” we discussed virtual patching, which is a method used by security vendors to protect devices against the latest vulnerability threats, without patching the application itself (by uploading new firmware, etc.). Usually, an IPS or a next-gen firewall will scan network traffic to detect attacks and block them before they reach the users’ vulnerable application. Thus, even though the application is not actually updated against the latest threats, it is still protected from them. Although this technique is commonly utilized in larger organizations and enterprise networks, it falls short when it comes to scenarios like remote work (“WFH”) or small businesses and SOHOs, as we will describe further.
Ensuring Uninterrupted Router Security: Who’s the Gatekeeper for Vulnerability Monitoring?
Hot patching can be compared to “hot swapping” in the central office, as in replacing a line card in a rack with the power still on, which means no network downtime when effecting a repair or upgrade. Hot patching then means you can protect your customers’ routers without them noticing it (which they would if their Wi-Fi and other connected items went offline for a while). Hot patching is based on what is known as “deep packet inspection,” or DPI. It’s a well-known and long-standing technique wherein the payload of packets traversing a data network is inspected. It can be used for traffic prioritization in Ethernet networks, and for security, “gate keeping” purposes. DPI differs crucially from static firewall protection, which is only filtering packets based on IP, ports, or protocols.
For example, a top-tier ISP recently conducted a large-scale operational test involving thousands of their routers to enhance security and quality of experience. As part of this test, they attempted to upload a new firmware file, but, thanks to real-time detection and monitoring, the hot patching feature detected an ‘unusual traffic pattern’ and blocked it.
DPI offers benefits such as:
- A much more active and “hands on” stance in that it looks into the payload itself
- DPI backed by extensive data sets on network traffic and equipment and augmented by AI and ML techniques enhances immediate detection and response
- Enables a network service provider to recognize patterns related to known or suspected attacks or hacking attempts, such as efforts to get into a network and “explore”
Further, the immediate detection and response advantage is key as it can take a lot of time for device manufacturers to provide patches or security firmware updates for their products.
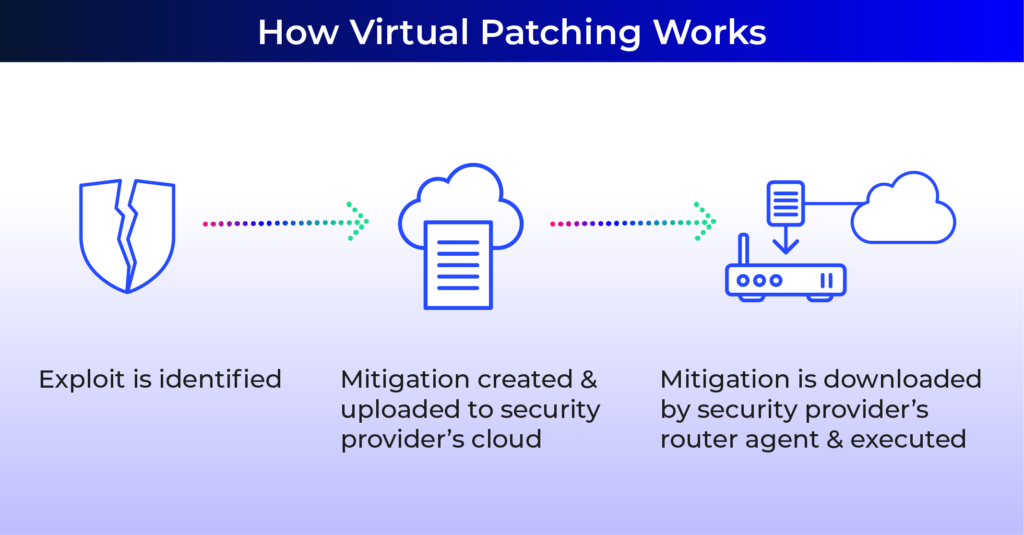
One reason, as mentioned at the top, is that is takes time to create a fix, to test it in the field, and then to distribute it. And for IoT devices it’s a different matter altogether, as numerous devices have minimal security and no ongoing security patch program. Or the devices are no longer on the market at all. This delay creates a significant window of opportunity for hackers who are well aware of these vulnerabilities and often have ample time to exploit them before the vendors issue a remedy, leaving end users vulnerable to attacks. Therefore, who should be in charge of monitoring those security vulnerabilities – the network owner or the network service provider?
Even when the patch is ready for deployment, there is still the question of how it will be deployed onto the users’ devices. Some devices can be updated via the corresponding app on the smartphone. Others, however, need to be updated manually – a lengthy and quite complicated process for even those who are tech savvy.
Minimizing Risk and Cost for Network Service Providers and Small Business Owners
You can make all these issues moot with a one stop protection program. By providing cybersecurity protection at the router or “CPE” level, including advanced hot patching capabilities, you can give your customers the peace of mind to focus on their business. You will become, in effect, their “automated CISO” by providing a significant value-added service beyond their basic connectivity bundle.
You can do this by adding a layer of automated security services incorporating hot patching and advanced DPI. As seen with Israel’s largest telco, Bezeq, and elsewhere, this layer can be implemented rather easily and seamlessly and it will eliminate all sorts of problematic scenarios, such as:
- End users (aka, your customers) waiting for weeks or months for “someone” to repair security holes and upload new firmware to their vulnerable devices
- Uncertainty regarding traffic patterns entering the “gateway keepers” (aka, the routers) of your customers’ networks
- Instructing your customers how to upload security patches of various types
- Devices no longer on the market – if they cannot be updated, then the only alternative usually is to discard them, which is bad for the environment too
- Supply chain issues – the process of determining if there’s a security problem with a chipset in a device, for instance, or the possibility that a network service provider might have to replace thousands of infected routers – which could cost a substantial sum of money
How much money? On the device manufacturers’ level, there are security solutions that take quite a bit of time to implement and can have a significant impact on production schedules and delivery of new equipment to service providers. This scenario would fall in the “time is money” category. As for real time expenditures, there have been recent cases in which a network service provider has had to deploy significant numbers of “field techs” to visit the homes of thousands of customers and swap out infected routers.
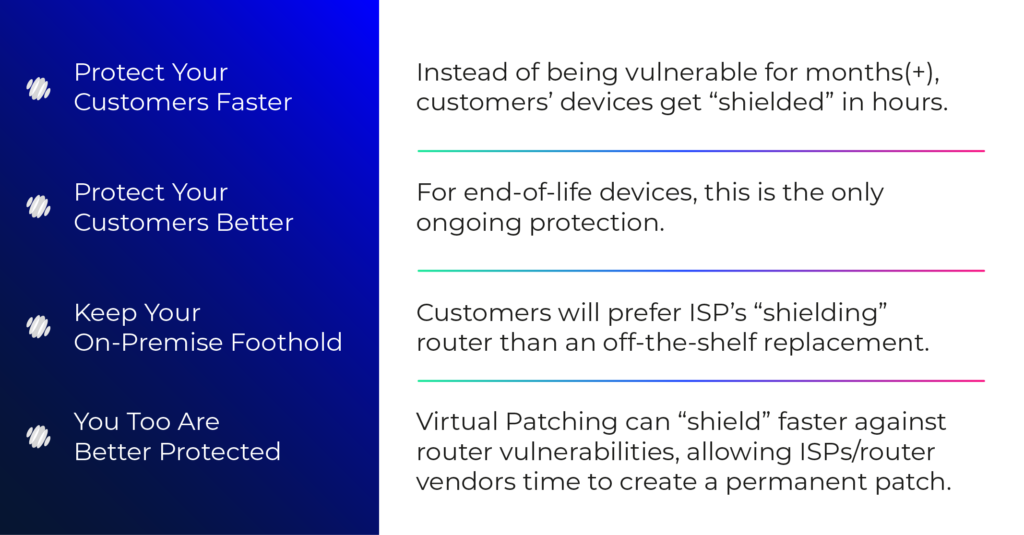
In conclusion, it is highly likely that malicious actors will try to hack unmanaged networks with little protection, such as those found in the homes and small businesses of your customers. By implementing hot patching, you can effectively mitigate all the aforementioned problematic scenarios. Field-tested and proven in real-world operating environments with leading network service providers across multiple countries, hot patching techniques provide a reliable solution. Don’t let a lack of IoT security become an open invitation for hackers. With hot patching, you can ensure constant real-time protection and empower your customers with comprehensive router and device security while eliminating the complexities of managing vulnerabilities and their fixes.







